
In an era where mergers, acquisitions and multi-academy consolidations are commonplace, centralising multiple domains into a single Microsoft 365 tenant delivers undeniable efficiencies in security, licensing and administration. Yet with consolidation comes the hidden risk of an unwieldy Global Address List (GAL) – a single directory that exposes every mailbox, group and resource across your entire tenant. For an education trust of a dozen schools, this can mean a teacher accidentally emailing safeguarding records to the wrong academy. For a merged enterprise, it may result in sensitive financial forecasts landing in a newly acquired subsidiary’s inbox.
This article presents a fully-up-to-date approach – using native Exchange Online Address Book Policies (ABPs) – to carve a monolithic GAL into secure, domain or division specific views You’ll gain:
Wherever possible, I’ve drawn directly from Microsoft’s latest documentation to ensure accuracy.
 Many organisations believe a centralised directory is inherently beneficial: one search bar to rule them all. In practice, users endure information overload when they must sift through hundreds or thousands of irrelevant entries to find a colleague or resource. Worse, autocomplete treats internal and external addresses the same, so a slip of the finger can expose confidential data to unintended recipients.
Many organisations believe a centralised directory is inherently beneficial: one search bar to rule them all. In practice, users endure information overload when they must sift through hundreds or thousands of irrelevant entries to find a colleague or resource. Worse, autocomplete treats internal and external addresses the same, so a slip of the finger can expose confidential data to unintended recipients.
For multi-academy education trusts, safeguarding student information is non-negotiable. A misplaced click can send pupil assessment data or pastoral notes to the wrong school, risking GDPR breaches and parental complaints. In corporate scenarios – say, a company acquiring a competitor – financial controllers might inadvertently share year-end bonus details with executives of the acquired entity. These are not hypothetical concerns; every mis-addressed email carries reputational damage, regulatory fines and erosion of stakeholder trust.
IT helpdesks bear the brunt of this chaos, fielding reported incident tickets such as “Why can’t I find Mrs Jones in my academy?” or “Why am I seeing rooms from the finance department?” These repetitive queries divert valuable IT capacity from strategic projects – be it rolling out a new learning-management system or deploying advanced security analytics. As tenant scale grows, so too do the hidden costs of a monolithic GAL.
 Rather than fragment your environment into separate tenants – an approach that multiplies licences, security boundaries and operational overhead – Exchange Online’s Address Book Policies (ABPs) offer a “virtual partition” within your existing tenant. An ABP bundles together four filtered directory view components so that users see only the objects assigned to their business unit or academy all while retaining centralised governance and compliance controls.
Rather than fragment your environment into separate tenants – an approach that multiplies licences, security boundaries and operational overhead – Exchange Online’s Address Book Policies (ABPs) offer a “virtual partition” within your existing tenant. An ABP bundles together four filtered directory view components so that users see only the objects assigned to their business unit or academy all while retaining centralised governance and compliance controls.
At its core, an ABP comprises:
By tagging mailboxes using a custom attribute or SMTP domain suffix you drive these filters automatically, so new users immediately inherit the correct ABP without manual reassignment. The Address Book Policy Routing agent further enforces isolation by marking out-of-scope lookups as “external” ﹘ preventing misleading “internal” display names in autocomplete once you enable it with:
Set-TransportConfig -AddressBookPolicyRoutingEnabled $true
When a user types a name into the To: field in Outlook or OWA, the directory lookup consults the GAL. A domain-specific GAL (e.g. GAL_Contoso) ensures that Division A staff resolve only their own colleagues, distribution lists and contacts. This scoping is driven by a recipient filter, most commonly mapping CustomAttribute1 to a division code, such as “Contoso”.
Outlook’s cached-mode clients download the OAB every eight hours by default. When you create an OAB that points to the same filtered GAL and address lists (e.g. OAB_Contoso), offline users maintain the same segmented experience even when disconnected from the network. This is critical for remote or bandwidth-constrained environments where cached-mode Outlook is the norm.
Resource mailboxes (meeting rooms, hot desks, equipment) often clutter the global directory. By creating a Room List object filtered on both the RecipientDisplayType (e.g. ConferenceRoomMailbox) and your division tag, you surface only the relevant rooms in meeting-room pickers preventing double bookings and administrative friction across units.
Under each GAL, you can present one or more Custom Address Lists for instance, “Finance Teams” or “Faculty Staff” using the same division filter. These lists appear as categories in Outlook’s address-book pane, enabling structured browsing rather than free-form search. Together, all four components weave a seamless, tailored directory experience for each business unit.
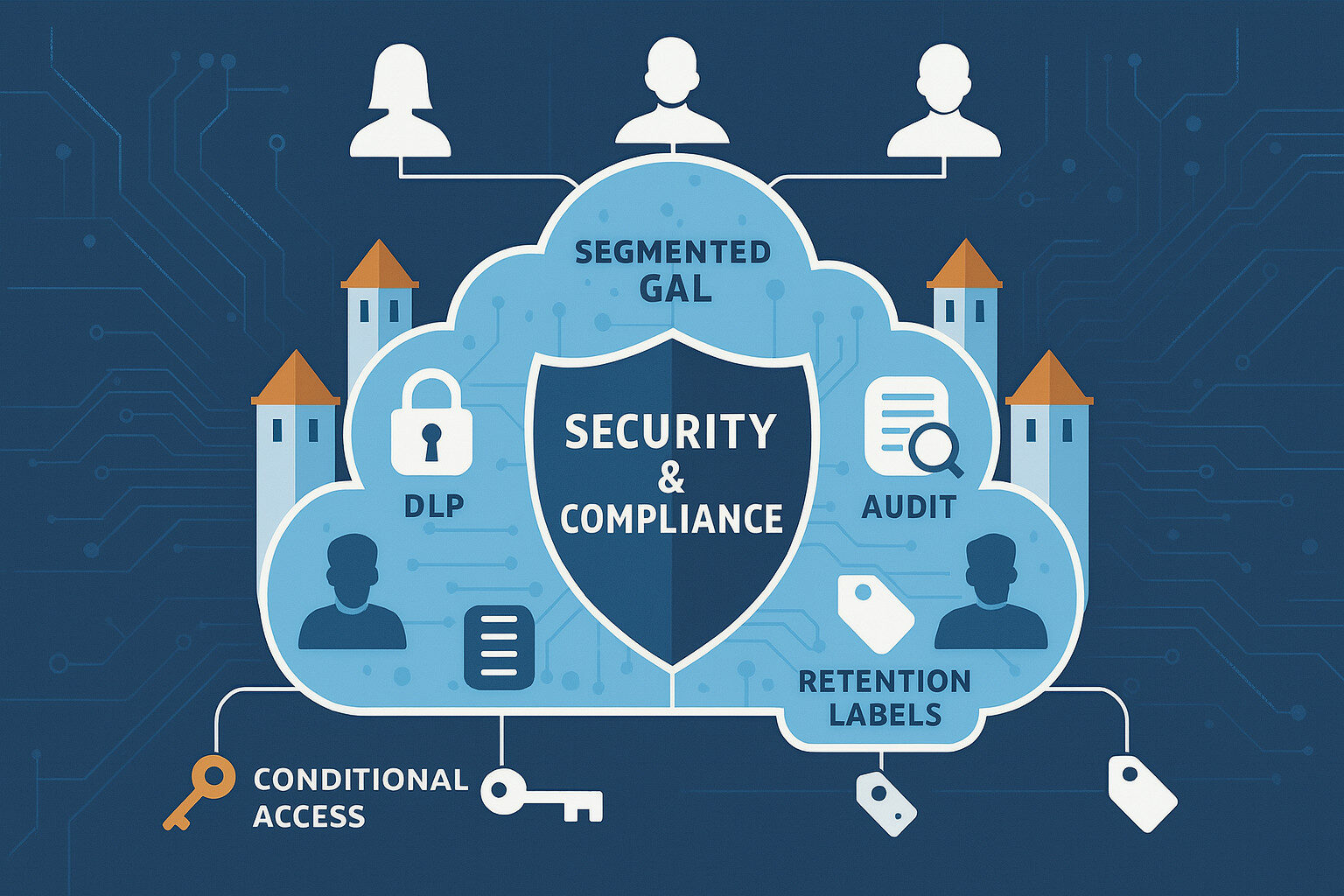 Segmentation does more than improve usability – it underpins your security and compliance strategy with multiple, reinforcing controls.
Segmentation does more than improve usability – it underpins your security and compliance strategy with multiple, reinforcing controls.
With a monolithic GAL, DLP policies must blanket the entire tenant, triggering false positives when users legitimately email across divisions. By contrast, ABP segmentation lets you craft targeted DLP rules that apply within each directory silo. For example, exam results can circulate freely within an academy but are blocked when addressed outside its ABP, sharply reducing administrative overhead in policy tuning and alert triage.
Segmented GALs shrink your search scope. Compliance officers can restrict Content Searches to a single ABP, slashing processing time and data volumes. In education trusts, this ensures that subject-access requests remain tightly confined to the relevant academy, a critical requirement under GDPR and UK data-protection regulations.
Exchange’s Admin Audit Logs record ABP assignments and changes. Paired with Entra ID sign-in logs and Microsoft Defender for Cloud App alerts, you gain a holistic view of who had directory view access and when; vital for ICO audits or GDPR/DPA reporting.
You can enforce stricter MFA or device compliance policies when users attempt to contact out-of-scope addresses, and automatically scope retention settings by ABP so that safeguarding incidents in one academy or financial approvals in one division inherit the correct retention label without manual intervention.
You don’t need to be a PowerShell maestro to stand up ABPs. Below are the core snippets, each accompanied by a clear explanation of what it achieves:
Get-Mailbox -Filter "WindowsEmailAddress -like '*@contoso.com'" | Set-Mailbox -CustomAttribute1 "Contoso"
This retrieves every mailbox with a primary SMTP in @contoso.com and sets its CustomAttribute1 to “Contoso”. This tag drives all subsequent filters.
New-AddressList -Name "AL_Contoso" -RecipientFilter "CustomAttribute1 -eq 'Contoso'"Defines a curated address list named “AL_Contoso” containing only objects tagged “Contoso”. Users see “AL_Contoso” in Outlook’s address-book pane.
New-GlobalAddressList -Name "GAL_Contoso" -RecipientFilter "CustomAttribute1 -eq 'Contoso'"Spins up a GAL called “GAL_Contoso” so that name resolution (autocomplete, To/Cc picker) consults only Division A objects.
New-OfflineAddressBook -Name "OAB_Contoso" -AddressLists "GAL_Contoso","AL_Contoso"Creates an OAB snapshot combining the filtered GAL and address list; Outlook cached-mode clients download this snapshot on their regular.
New-AddressList -Name "Rooms_Contoso" -RecipientFilter "(RecipientDisplayType -eq 'ConferenceRoomMailbox') -and (CustomAttribute1 -eq 'Contoso')"Isolates only room-mailboxes tagged “Contoso,” ensuring users book only local facilities.
New-AddressBookPolicy -Name "ABP_Contoso" `
-GlobalAddressList "GAL_Contoso" `
-AddressLists "AL_Contoso","Rooms_Contoso" `
-OfflineAddressBook "OAB_Contoso" `
-RoomList "Rooms_Contoso"Get-Mailbox -Filter "CustomAttribute1 -eq 'Contoso'" | Set-Mailbox -AddressBookPolicy "ABP_Contoso"
Packages your filtered GAL, address lists, OAB and room list into ABP_Contoso, then assigns it to all Division A mailboxes. From that moment on, those users experience a personalised directory.
Set-TransportConfig -AddressBookPolicyRoutingEnabled $trueEnsures attempts to resolve addresses outside a user’s ABP show as “external,” preventing confusing “internal” display names.
 While ABPs natively govern Exchange Online and Outlook, modern organisations demand consistent directory experiences across Microsoft 365. In Microsoft Teams, you can propagate ABP scoping so that chat look ups, @mentions and the people picker respect your segmented GALs:
While ABPs natively govern Exchange Online and Outlook, modern organisations demand consistent directory experiences across Microsoft 365. In Microsoft Teams, you can propagate ABP scoping so that chat look ups, @mentions and the people picker respect your segmented GALs:
Within a few hours, Teams people search, chat look-ups and meeting invitations will honour your ABPs so Contoso staff no longer see Fabrikam colleagues in their directory. Remember to test across desktop, web and mobile clients, as propagation timing can vary.
Beyond Teams, many organisations leverage Planner, SharePoint, OneDrive and Power Platform. While these services don’t natively enforce ABPs, you can approximate segmentation by:
For Viva Engage, employ security groups and administrative unit scoped policies in Microsoft Entra ID so that communities auto-populate only with correctly tagged users. A brief proof-of-concept helps uncover any integration gaps and informs / validates your rollout timeline.
 A reliable ABP deployment is not a “set and forget” exercise – it demands a structured governance model encompassing onboarding, offboarding, drift detection and change control.
A reliable ABP deployment is not a “set and forget” exercise – it demands a structured governance model encompassing onboarding, offboarding, drift detection and change control.
Integrate your HR or identity-management system to map each new employee’s “DivisionCode” into a Microsoft Entra ID extension attribute (synchronised as CustomAttribute1 in Exchange Online). Embed ABP assignment into your provisioning scripts so that mailboxes arrive correctly scoped on day one.
On the flip side, your leaver process must clear the attribute and ABP, then disable the mailbox:
Set-Mailbox -Identity $UPN '
-AddressBookPolicy $null
Set-Mailbox -Identity $UPN '
-CustomAttribute1 $null
Disable-Mailbox -Identity $UPN
This prevents stale objects from cluttering your OAB and polluting directory views.
Schedule a daily or weekly automated scan using Exchange Online PowerShell or Microsoft Graph, to flag mailboxes whose CustomAttribute1 mismatches their SMTP domain or ABP assignment. Generate a Policy Drift Report (CSV or HTML) and surface it in your IT dashboard (e.g. Power BI) so operations staff can remediate before users report issues.
Store all scripts, runbooks and policy definitions in a version-controlled repository (Azure Repos or GitHub Enterprise). Maintain a living Governance Guide that defines:
Leverage Administrative Units in Microsoft Entra ID to grant scoped management permissions. Assign local IT or academy leads the minimal roles needed to update CustomAttribute1 and ABP assignments for their own school or organisation – minimising the risk of accidental tenant-wide changes. Regularly review administrative unit assignments (at least quarterly) to ensure only current, authorised personnel retain access.
Address Book Policies transform your Microsoft 365 tenant’s Global Address List from a sprawling, chaotic directory into a finely segmented, domain or academy centric experience. For education trusts, this reinforces safeguarding and data-protection by preventing cross-academy data leakage. For multi-domain businesses, it secures sensitive M&A information and financial records within proper silos.
By combining clear PowerShell implementation patterns, expanded security and compliance benefits, Teams-wide scoping and a robust governance framework complete with Microsoft Entra ID Administrative Units, you will deliver a seamless, secure directory experience.

Microsoft Solution Architect, Senior Project Manager, and Mental Health Advocate